Threat focus
This area lists all vulnerabilities ③ that are known for supported assets from the inventory. When you click on a vulnerability, additional details about it ④ are shown.
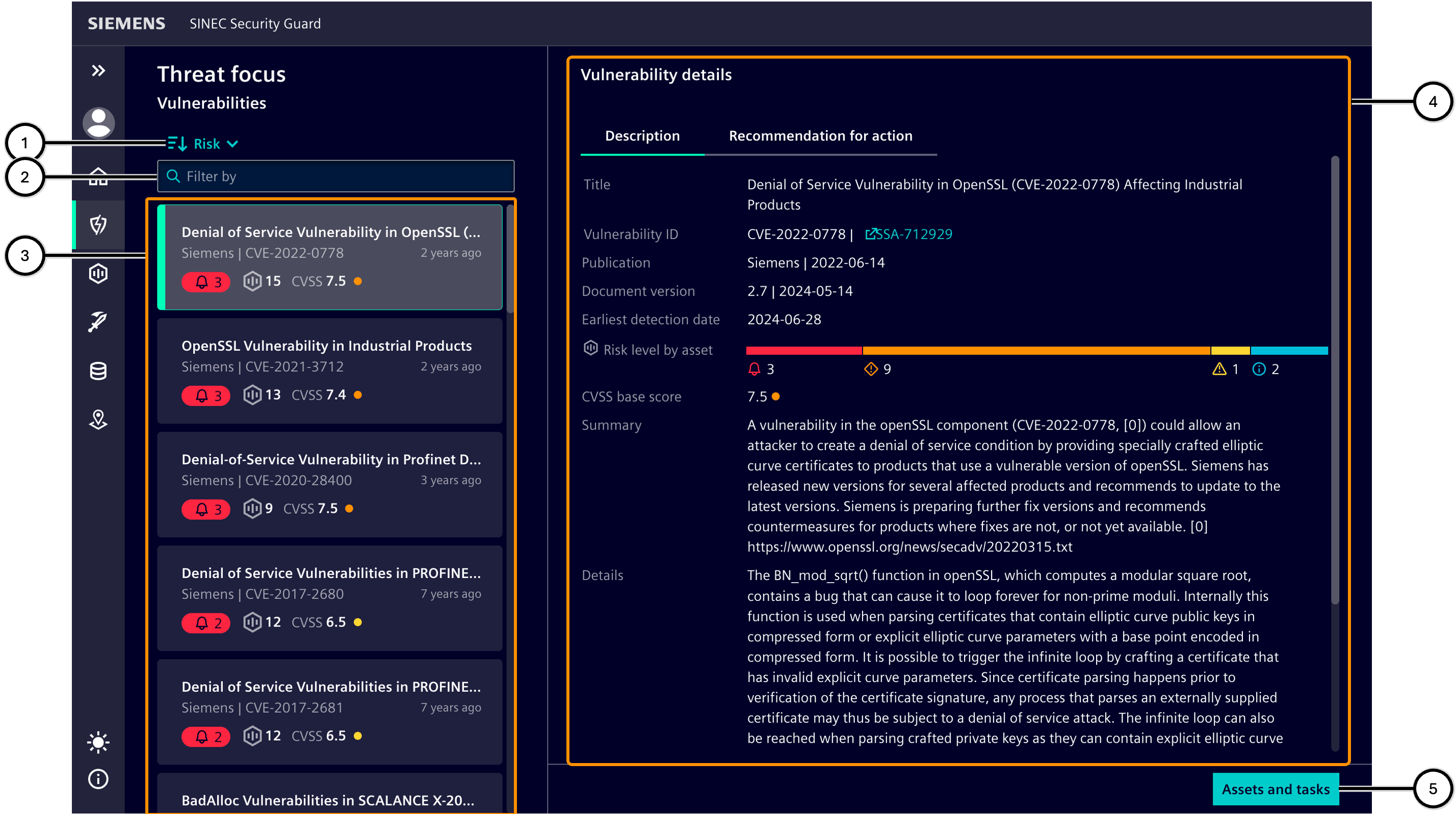
| Icon | Description |
|---|---|
| ① | Sort order selection button |
| ② | Input field for filtering the vulnerabilities |
| ③ | List of existing vulnerabilities |
| ④ | Details of the selected vulnerability |
Vulnerability
Additional information is displayed for each vulnerability.
The CVSS rating is as follows:
| Rating | CVSS score | Color coding |
|---|---|---|
| None | 0.0 | (none) |
| Low | 0.1 – 3.9 | Blue |
| Medium | 4.0 – 6.9 | Yellow |
| High | 7.0 – 8.9 | Orange |
| Critical | 9.0 – 10.0 | Red |
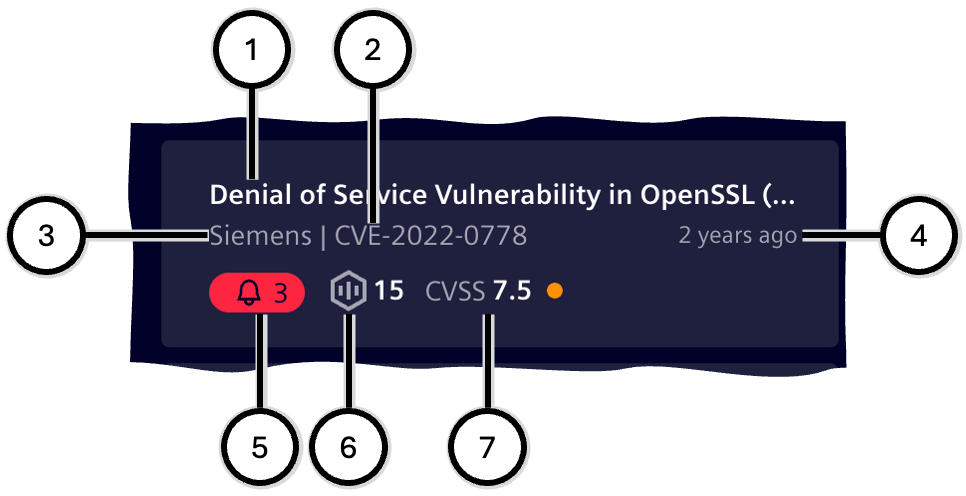
| Icon | Description |
|---|---|
| ① | Title of the vulnerability |
| ② | ID of the vulnerability |
| ③ | Publisher of the vulnerability description |
| ④ | Age of the vulnerability description |
| ⑤ | Total risk level: Highest risk and number of assets affected by the highest risk |
| ⑥ | Total number of assets affected by this vulnerability, across all risk levels; this total number also includes the assets affected by the total risk level |
| ⑦ | CVSS score of the vulnerability; the value is also shown in color |
Details of the selected vulnerability
Only information related to assets included in the inventory is displayed.
Description
This area shows information about the description of the vulnerability as well as its impact and occurrences on assets in the plant; see 'Threat details'. This area shows options to fix the vulnerability or at least to reduce its impact or lessen the vulnerability; see 'Threat details'.
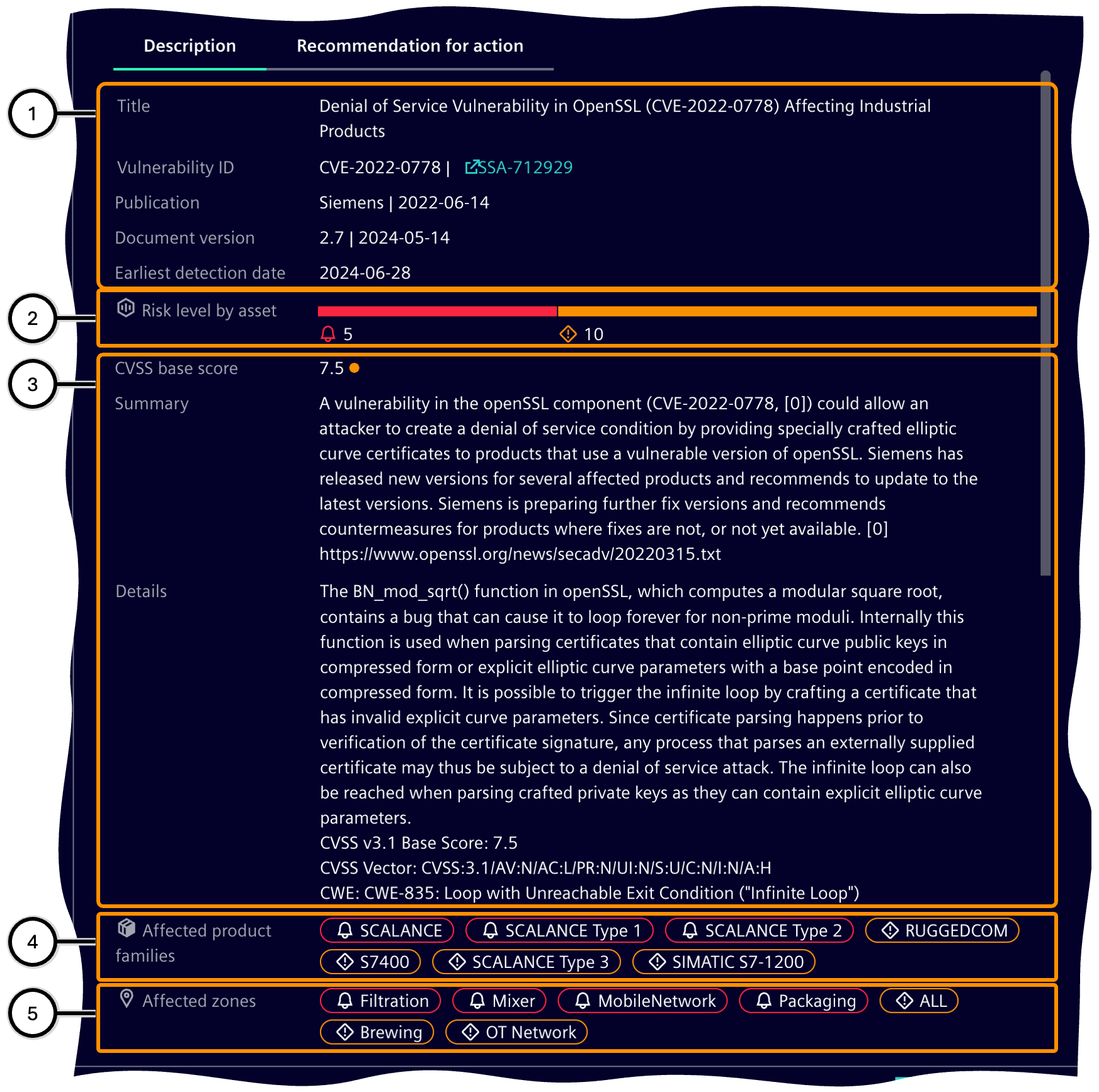
| Icon | Description |
|---|---|
| ① | Information on the origin of the vulnerability |
| ② | Distribution of the individual risk levels over all of the affected assets; see color bar for risk level. |
| ③ | Information on the effects of the vulnerability |
| ④ | Product families affected by the vulnerability |
| ⑤ | Zones affected by the vulnerability |
Recommended action
This area shows options to fix the vulnerability or at least to reduce its impact or to lessen the vulnerability.
The list of affected products and solutions describes each product with affected firmware versions and the corresponding solution; the link leads to the product page, from where a newer firmware version can be downloaded if necessary.
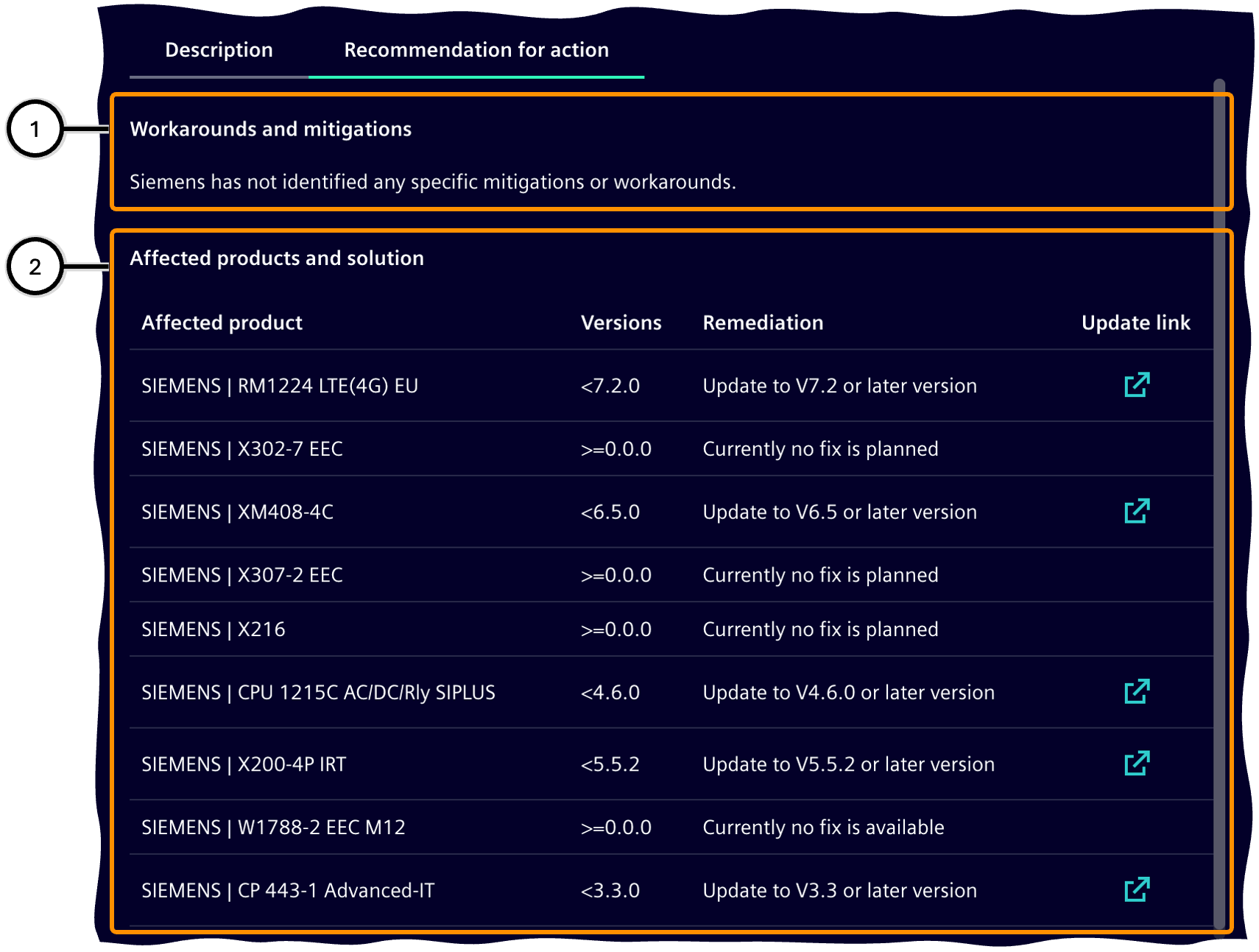
| Icon | Description |
|---|---|
| ① | Workarounds and mitigation |
| ② | List of affected products and solutions |