Recurring elements
Color bar for risk level
The color bar for the risk level is displayed in various places, e.g., in the 'Threat focus' or in the zone information of the 'Asset focus'.
The color bar indicates which risk levels apply to a group of assets.
In its upper half, the bar shows segments with corresponding coloring, e.g., a long red bar (for the 54 assets with 'Critical' risk level), a very short gray one (1 asset with 'Undefined'), etc. The length of the colored bar segments corresponds to the proportion of their status in the total amount. In the example, 54 assets have a 'Critical' risk level, 4 asset 'High', 0 assets 'Medium', 16 assets 'Low', and 1 asset 'Undefined'. Risk levels which do not apply are not shown at all.
A segment can be dashed, solid, or both:
- Fully dashed: All assets with that risk level already are managed.
- Fully solid: All assets with that risk level are still unmanaged. In the example, all 16 assets with 'Low' ③ and the 1 asset with 'Undefined' ④ are still unmanaged.
- Partially dashed and solid: Some assets of the given risk level are already managed, others aren't. In the example, from the 54 assets with risk level 'Critical' ① there is 1 asset already managed, 53 aren't; and from the 4 assets with risk level 'Critical' ② there is 1 asset already managed (see dashed part ⑥), 3 aren't.
In the lower half of the color bar, the corresponding colored symbol and the amount of assets ⑤ are displayed.
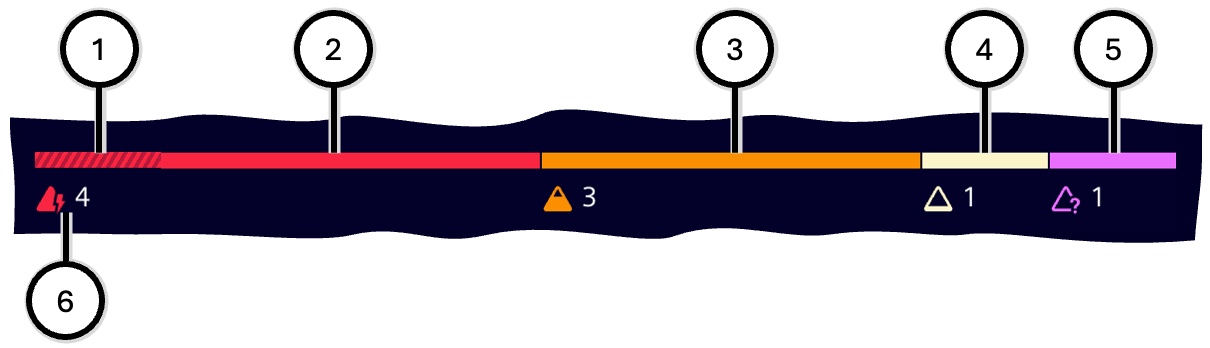
| Number | Color | Risk Level | Description |
|---|---|---|---|
| ① | Dashed | - | Dashed bar is shown for the number of assets which are already managed |
| ② | Red | Critical | |
| ③ | Orange | High | |
| (Not shown) | Yellow | Medium | |
| ④ | White | Low | |
| ⑤ | Purple | Undefined | |
| ⑥ | - | - | For each existing risk level: Corresponding symbol of affected asset and their number |
Managing progress
Progress bars appear in various places in SINEC Security Guard. They show how many assets are completely managed (all asset-vulnerabilities are set to managed) compared to the total number of assets.
On managing progress bars which depict assets from a certain risk level ②, dashed and solid areas depict the relation of already managed to still unmanaged assets (from the 5 assets in the example, 2 assets are already managed, 3 assets are still unmanaged).
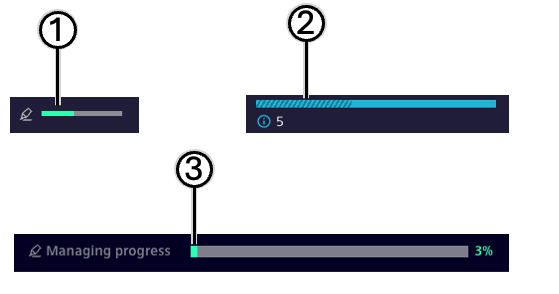
| Number | Description |
|---|---|
| ① | Progress of managing for an entity (vulnerability/product) |
| ② | Managing progress (dashed) compared to total number of assets with certain risk level |
| ③ | Managing progress in current view |
Asset details
The 'Asset details' can be closed with button ③. If you have opened a list of assets from the asset details, switch to the previous or next asset with its details using buttons ①.
The 'Product information' ④ shows information about the general product type. This information usually does not change when you switch to the details of another asset of the same model.
The 'Asset information' ⑤ shows information about the specific individual asset. This information will differ from the information of other assets, regardless of whether it is an asset of the same model or a completely different product.
The 'Network interfaces' ⑥ display all known information. If the asset has multiple interfaces, all are listed accordingly.
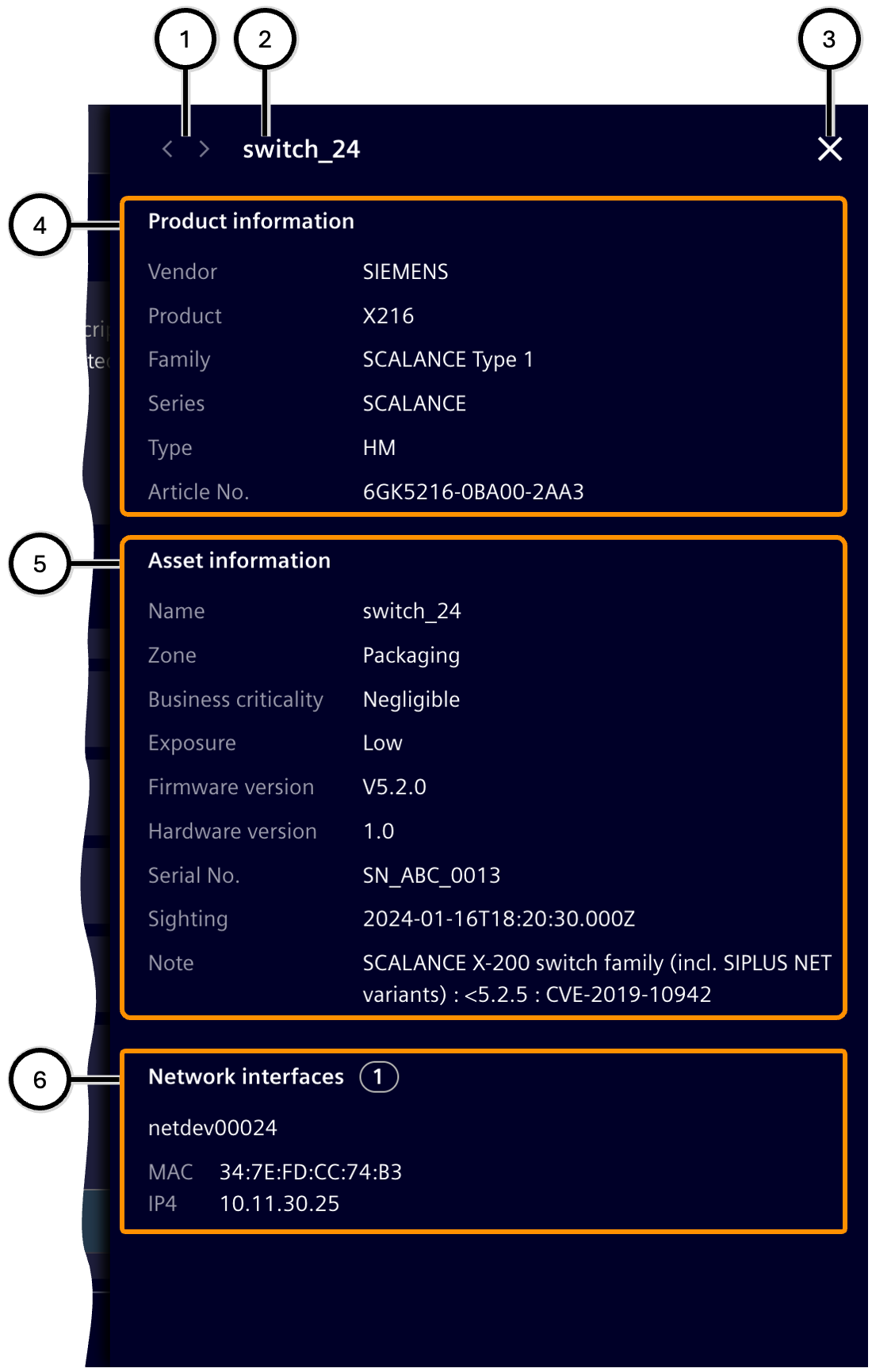
| Number | Description |
|---|---|
| ① | Navigation buttons |
| ② | Asset name |
| ③ | Button to close the asset details |
| ④ | Information related to the product type |
| ⑤ | Information related to the specific asset |
| ⑥ | Network interfaces |
Threat details
The view of the Threat details shows information about the description of the vulnerability as well as its penetration and relevance to the facility. It appears in the following variants:
-
as a large-scale view in 'Description' of Details of the selected vulnerability
-
as additional information in 'Threats and tasks'; here, there is an additional header with navigation options and information (⑥-⑧).
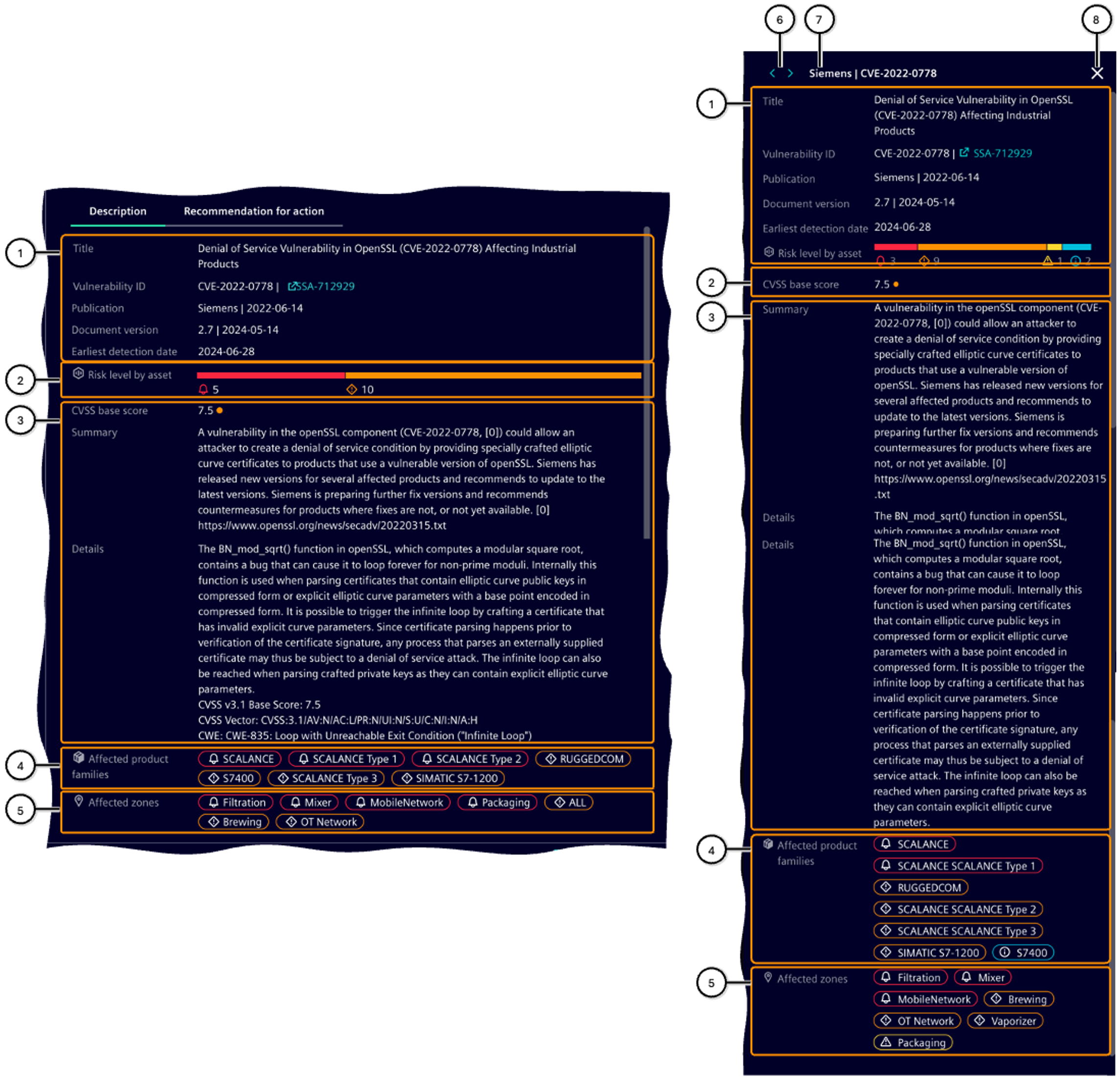
| Number | Description |
|---|---|
| ① | Information about the source and classification of the vulnerability |
| ② | Distribution of the individual risk levels across all affected assets |
| ③ | Detailed description of the vulnerability |
| ④ | Product families in the facility affected by the vulnerability |
| ⑤ | Zones in the facility affected by the vulnerability |
| ⑥ | Navigation buttons |
| ⑦ | Organization that published the vulnerability (ID) |
| ⑧ | Button to close the vulnerability details |
Checking user input
SINEC Security Guard checks all user inputs and outputs whether the input meets the criteria. Such checks can occur:
-
immediately after entering a character
-
upon leaving the input field
-
upon exiting the dialog or step
These feedback options are possible:
| Design | Example | Effect |
|---|---|---|
| Not checked / Initial state |  |
If the field requires input and is left empty, it changes to the 'Checked - Error' state |
| Tested - Error |  |
This field prevents the dialog from closing (Note: The shown error appears as in this example there is already another zone called "Brewing") |
| Tested – Error-free |  |
This field does not prevent the dialog from closing |