Asset focus
This area lists all zones, products, and assets from the inventory for which at least one vulnerability is known. Assets that are free of vulnerabilities are not displayed.
You can display all vulnerabilities of the selected asset and define appropriate tasks.
Zone overview
This area lists the zones affected by vulnerabilities ② and shows how they are affected ⑤. Clicking on a zone opens the 'Assets list'.
You can filter zones ① or adjust the sorting of zones ③.
Additional information is provided for each zone (④-⑦).
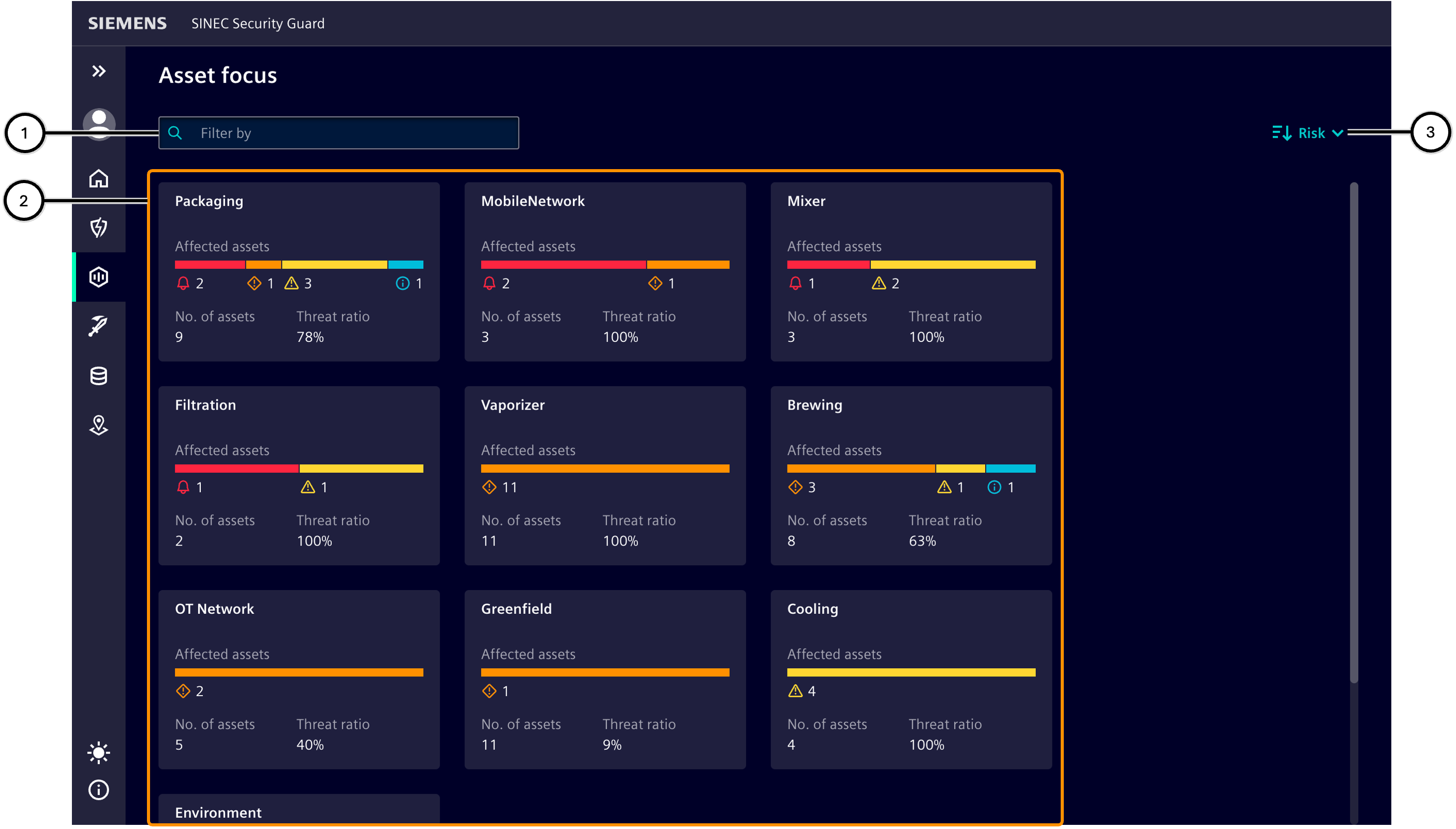
| Number | Description |
|---|---|
| ① | Input field for filtering the zones |
| ② | List of zones |
| ③ | Sort button |
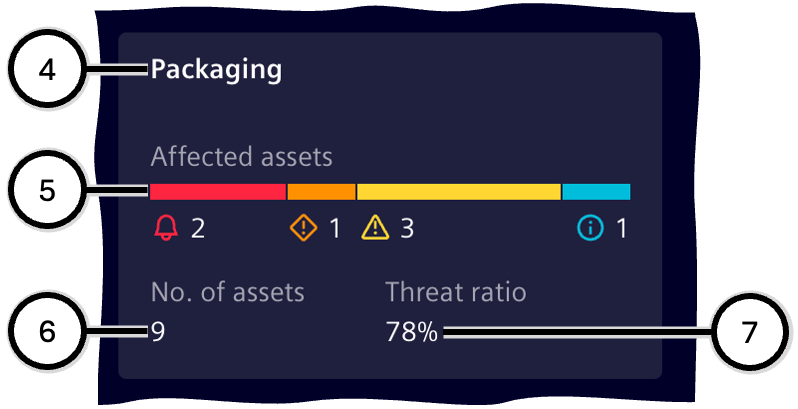
| Number | Description |
|---|---|
| ④ | Zone name |
| ⑤ | Distribution of the individual risk levels over all of the affected assets; see color bar for risk level. |
| ⑥ | Number of assets in this zone affected by at least one vulnerability. |
| ⑦ | Ratio between a) the total number of assets in this zone and b) the number of affected assets in this zone; at '100%', every asset contained in the zone is affected by at least one vulnerability. |
Asset list for zones
This area shows information about the selected zone as well as all products and assets in the inventory that are part of the zone and affected by at least one vulnerability.
Clicking the button ① takes you back to the 'Zone overview'.
The zone details ② show important information about the zone.
The list of products ③ shows products that contain at least one asset that is in the zone and is affected by a vulnerability. Clicking on it displays all affected assets ④. Details can be displayed for a selected asset ⑥.
After you select an asset and then navigate to the 'Threats and tasks' area ⑥, all vulnerabilities of the selected asset can be viewed and appropriate tasks can be defined. For each affected asset, the greatest risk level due to the currently pending vulnerabilities ⑦ is shown. It also shows how many of these pending vulnerabilities are still in the 'Open' status, and what the highest risk level of the open vulnerabilities is ⑩.
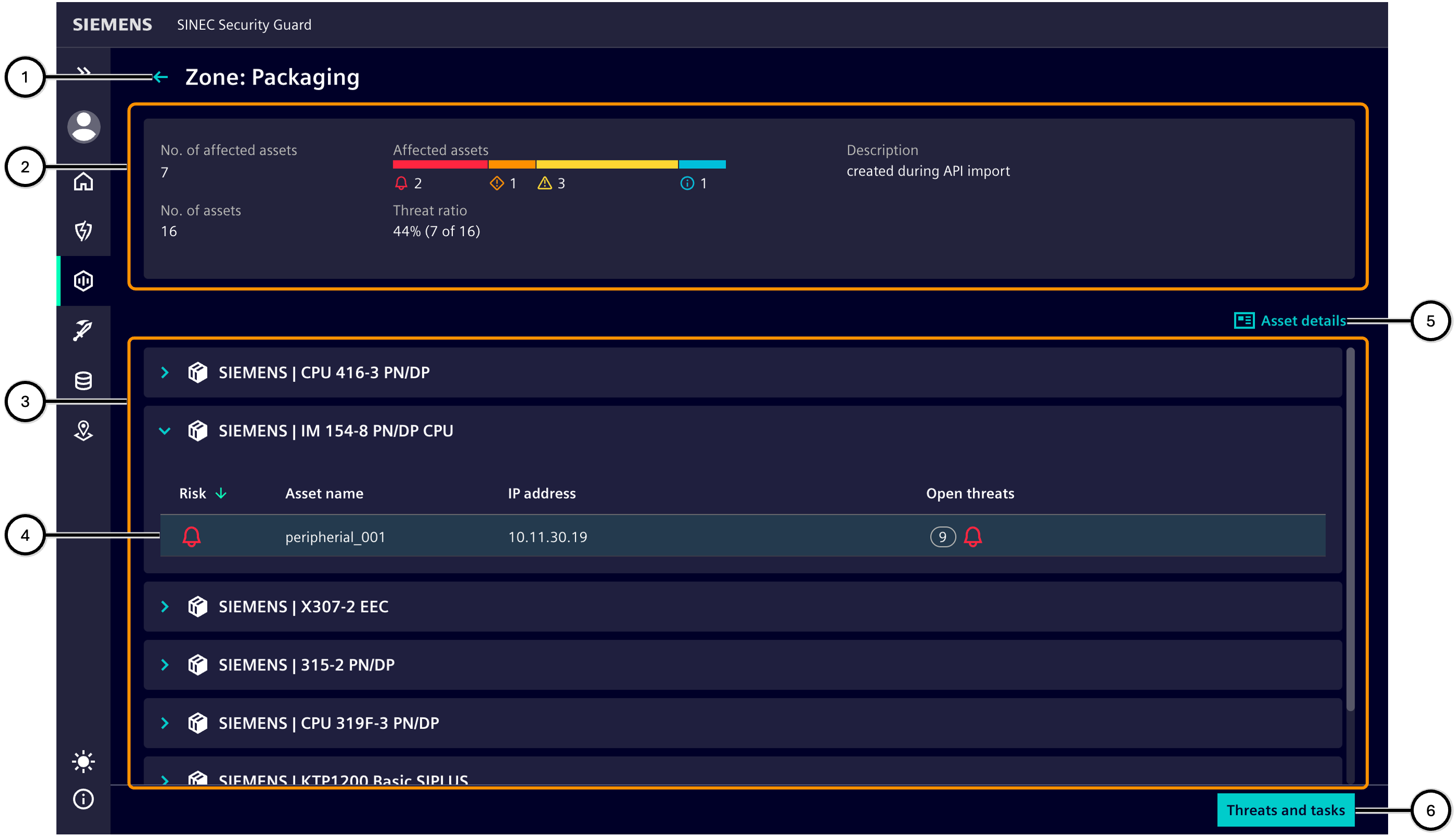
| Number | Description |
|---|---|
| ① | Name of the selected zone and navigation back to the 'Zone overview' |
| ② | Zone details display important information about the zone |
| ③ | List of products affected by vulnerabilities |
| ④ | Highest risk level of the assets of the respective product |
| ⑤ | Button to switch to 'Threats and tasks' |
| ⑥ | Display of asset details |

| Number | Description |
|---|---|
| ⑦ | Highest risk level due to an unfixed vulnerability on this asset |
| ⑧ | Asset name |
| ⑨ | IP address of the asset |
| ⑩ | Number and highest risk level of 'Open Threats' |
Asset overview
Assets-tab ② in Asset focus shows all the vulnerable assets regardless of zone assignment. This view allows quick search for the specific asset.
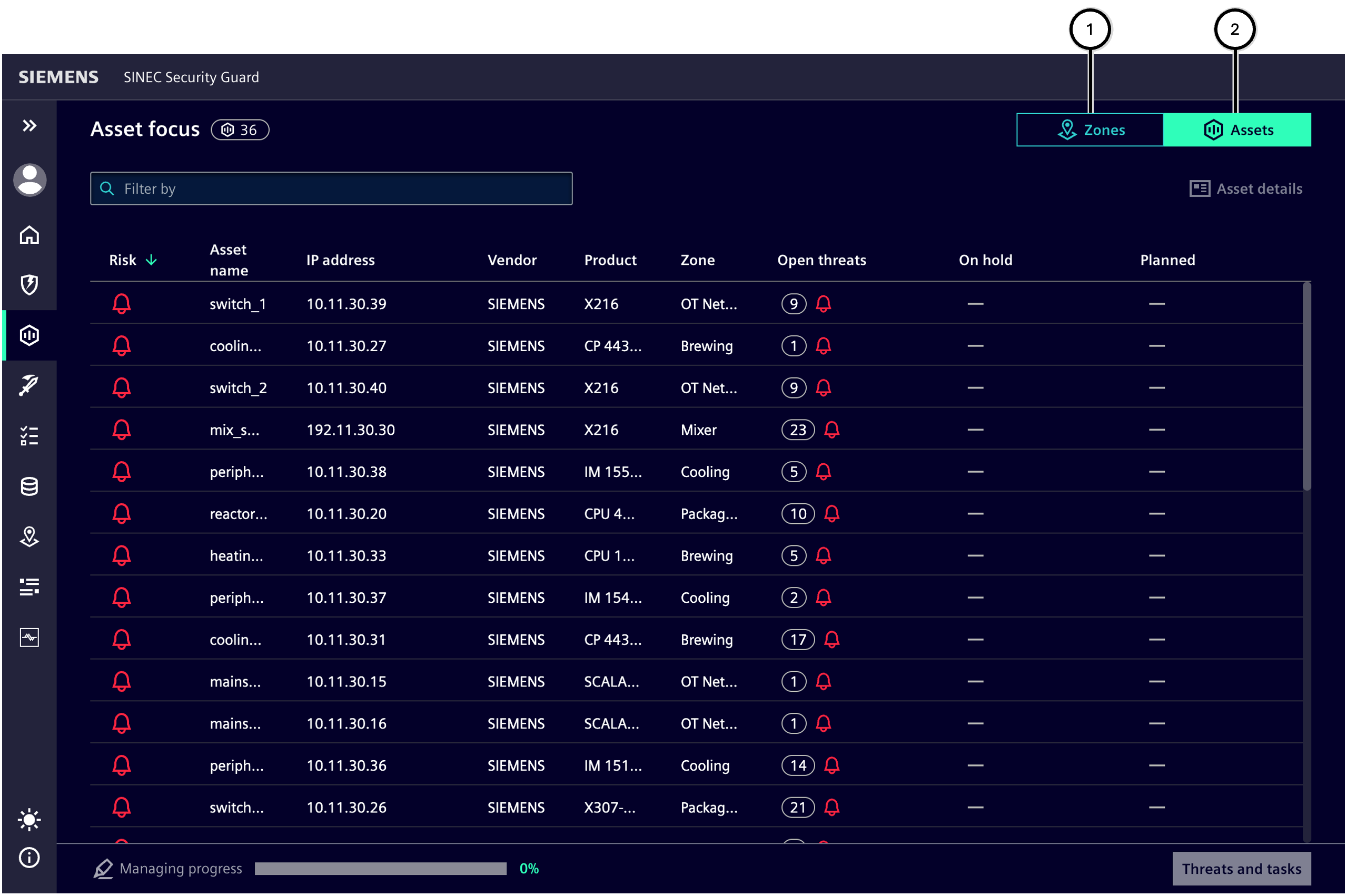
| Number | Description |
|---|---|
| ① | Zones-tab displays asset risk information grouped by zone |
| ② | Assets-tab displays all the assets affected by vulnerabilities in the system |
Threats and tasks
This section allows you to create tasks for a device based on the vulnerabilities it is exposed to. It is divided into four sections:
- Asset information ①,
- Vulnerabilities and Possible Countermeasures ②,
- Task list ③,
- Managing progress and additional functions ④.
To efficiently address the vulnerabilities of a device, the following steps are recommended:
- Review the device information ① to ensure the correct device is being processed.
- Examine the information in the 'Active' status group in the "Vulnerabilities and Possible Countermeasures" section ②: a. Firmware should always be up to date – many vulnerabilities can already be resolved by installing the latest firmware version. If the installed firmware is outdated, a corresponding task should be added to the Task list ③; all vulnerabilities that would be resolved by the firmware update will automatically be marked as 'Planned'. b. All untreated vulnerabilities should be reviewed one by one, and corresponding tasks to address the vulnerabilities should be added to the Task list ③. c. Once the status of a vulnerability changes from 'Open' to 'Planned', this will be reflected in all SSG statistics – such as in the progress ④ or on Home.
- Review all tasks in the Task list ③: a. Avoid conflicting tasks; if necessary, remove tasks and/or add a well-formulated custom task. b. Remove duplicate tasks. c. Edit tasks (e.g., adjust priority) until the entirety of the tasks in the Task list is meaningful. d. Link all tasks to all vulnerabilities they are needed to address, and adjust priority if necessary.
- Publish the Task list ④. This transfers all tasks in the list to the Task management – changing these tasks in the 'Vulnerabilities and Tasks' section is no longer possible.
- If necessary, navigate back to the device list in the device information ① to address the vulnerabilities of another device.
- Once all tasks are defined and published as desired, they can be further processed in the Task Management.
The overview illustrates a rough process:
- A device has untreated vulnerabilities for which no tasks have been defined yet; the progress is 0%.
- Tasks have been planned for some vulnerabilities, some of which have already been published; the progress is greater than 0% but not yet 100%.
- Tasks have been planned for as many vulnerabilities as possible, and all tasks are published; ideally, the progress is 100%, but sometimes it may be less.
- The Task management shows the published tasks. Here, they can be marked as 'Implemented' after completion. This marks the vulnerability as resolved.
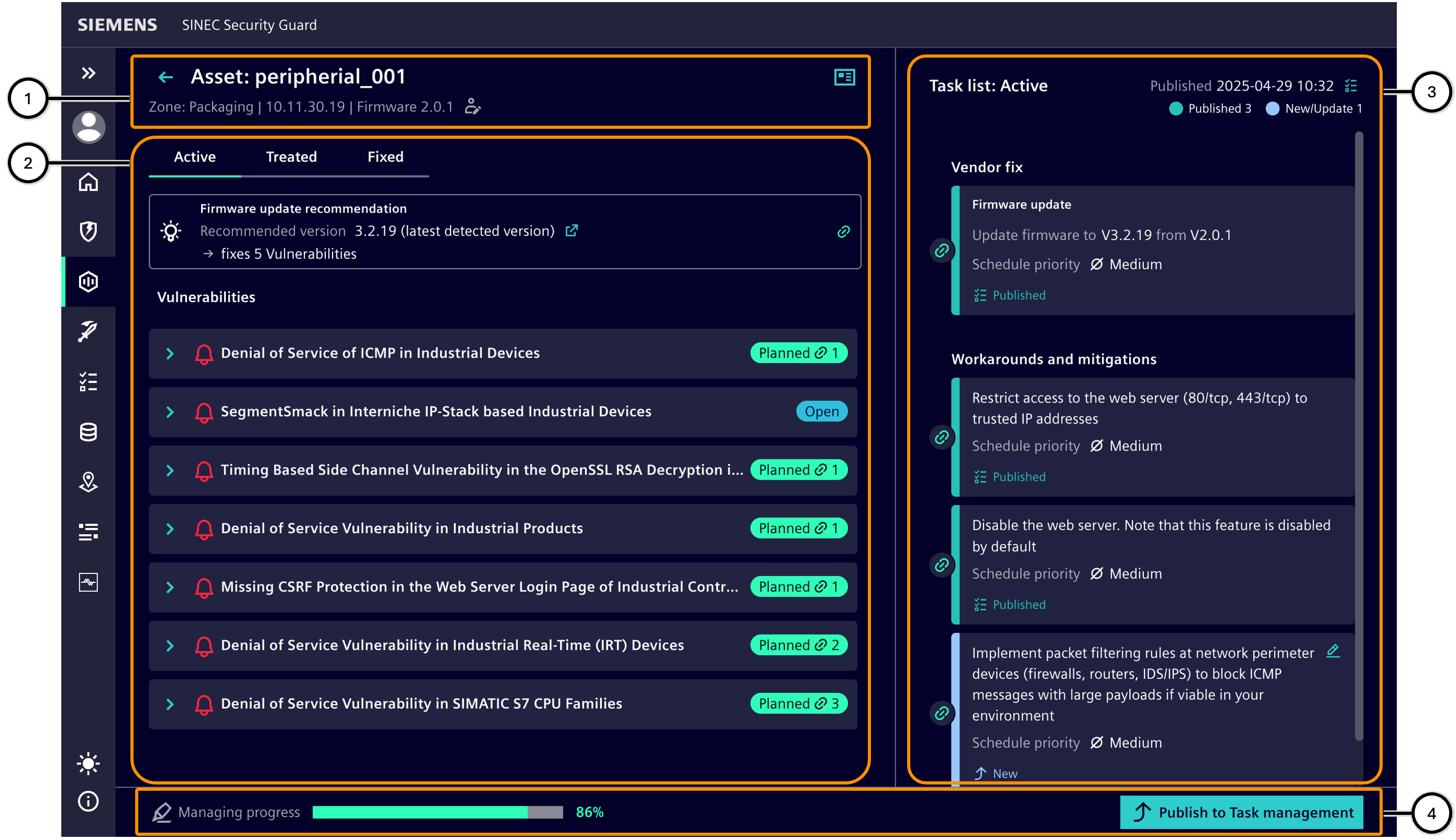
| Number | Description |
|---|---|
| ① | Device information |
| ② | Vulnerabilities related to the device |
| ③ | Tasks planned for the device |
| ④ | Information on progress and additional functions |
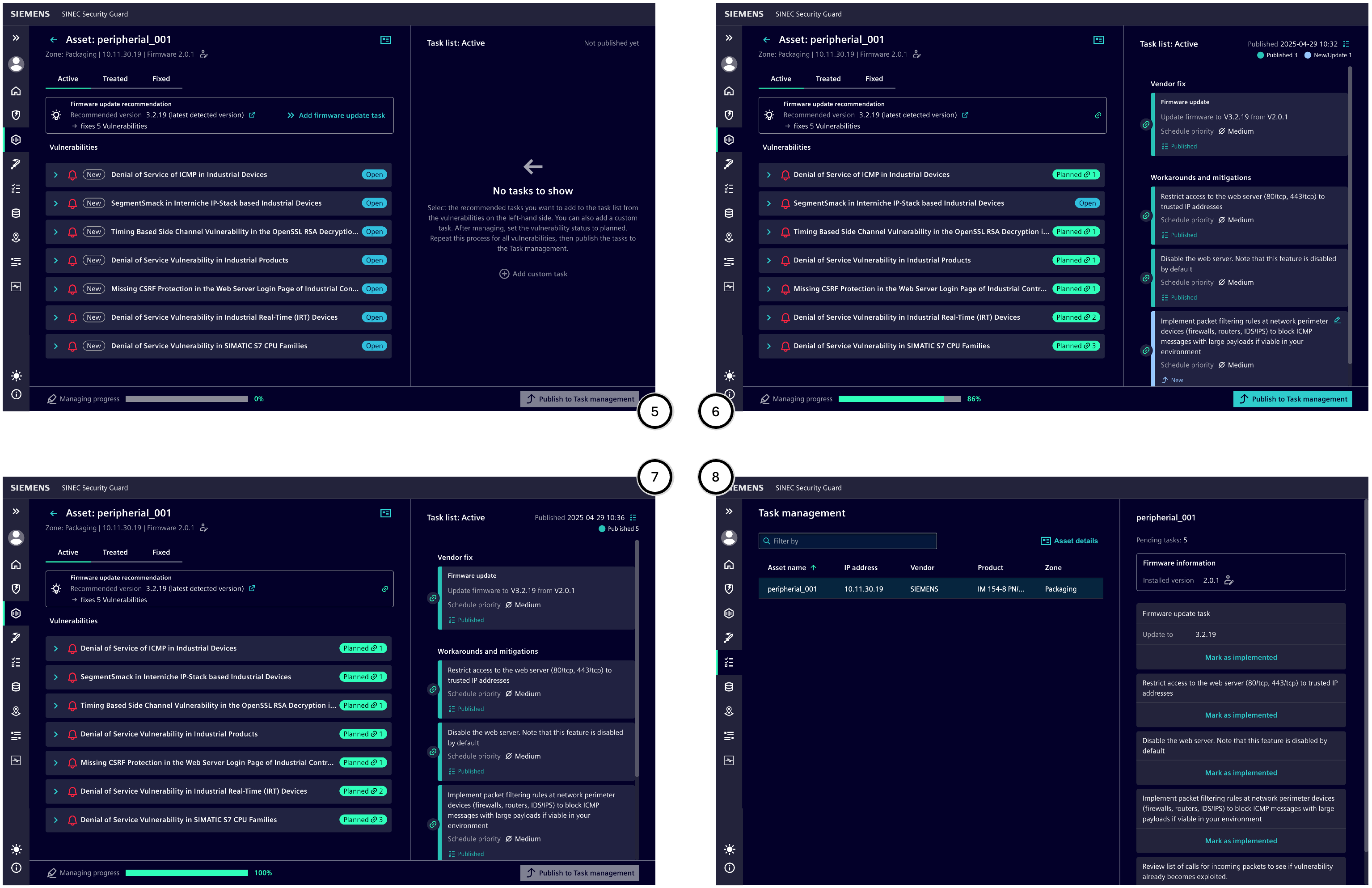
| Number | Description |
|---|---|
| ⑤ | Example state of a device in 'Vulnerabilities and Tasks' before processing |
| ⑥ | Example state after partial processing |
| ⑦ | Example state after complete processing |
| ⑧ | Example state of tasks for a device in 'Task Management' |
Asset information
This area provides information about the affected device and displays its name ②, the zone ④, the IP address ⑤, and the currently installed firmware version ⑥; if the firmware version of the device has been manually edited, this is indicated accordingly ⑦. Additional information is displayed with the 'Device details' button ③.
Clicking the back button ① navigates back to the device list.
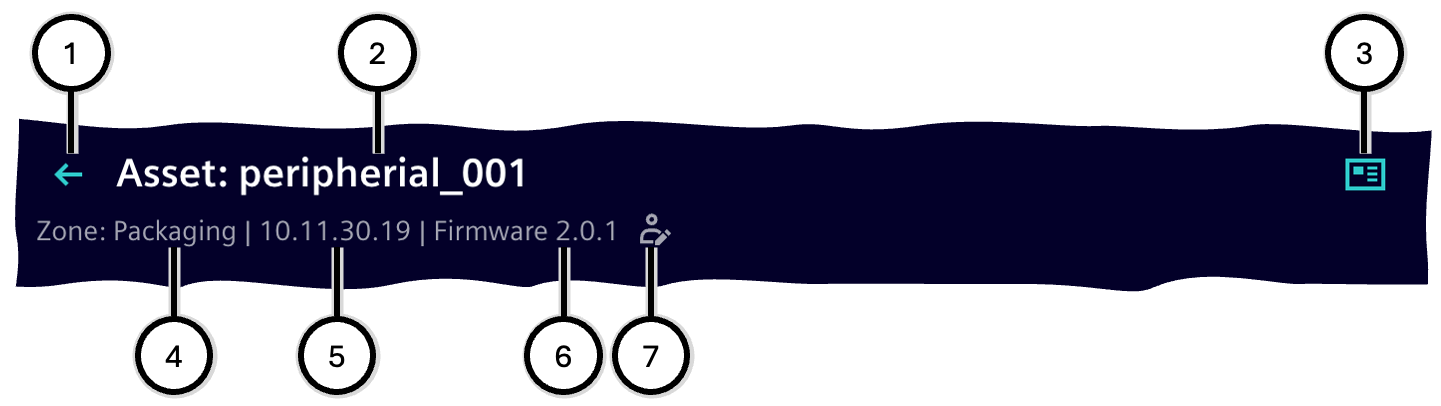
| Number | Description |
|---|---|
| ① | Button 'Back to device list' |
| ② | Device name |
| ③ | Button 'Device details' |
| ④ | Name of the device's zone |
| ⑤ | IP address |
| ⑥ | Version of the currently installed firmware |
| ⑦ | Optional note if the firmware version has been manually changed |
Vulnerabilities and possible countermeasures
This area provides information about vulnerabilities that compromise the security of the device and offers possible countermeasures to address them.
Status groups
The managing status of a vulnerability is defined by the evaluation of the vulnerability and the planning and execution of countermeasures. Status groups help to keep track of vulnerabilities: Each status group gathers vulnerabilities according to their respective managing status, allowing users to specifically display, for example, all vulnerabilities that still pose an acute threat.
Only those status groups additionally show the number of vulnerabilities they contain where the goal is an empty list.
| Status group | Managing status | Applied status |
|---|---|---|
| Active | Displays all vulnerabilities that have not yet been fully processed | 'Open', 'Planned' |
| On hold | Displays all vulnerabilities for which a temporary decision had been taken | 'Risk accepted till…', 'Remediation blocked', 'Asset removal planned', 'Postponed' |
| Treated | Displays all vulnerabilities for which the user has decided to take no action | 'Obsolete by Implementation', 'Not Relevant', 'Resolved' |
| Fixed | Displays all vulnerabilities whose tasks have already been completed | 'Fixed' |

| Number | Description |
|---|---|
| ① | Status group 'Active' with the number of vulnerabilities it contains |
| ② | Status group 'On hold' with the number of vulnerabilities it contains |
| ③ | Status group 'Treated' |
| ④ | Status group 'Fixed' |
Status group 'Active'
This status group displays vulnerabilities that are currently active. Tasks can be planned to address these vulnerabilities.
Planning tasks is only possible for vulnerabilities in the 'Active' status group.
Firmware update
The 'Firmware Update' object displays information about the current firmware status of the device:
If a newer firmware version is available to address vulnerabilities than the currently installed one, the 'Firmware Update' object is displayed with the following information:
- Version of the latest firmware to address vulnerabilities ① with an optional download link ②
- Number of vulnerabilities resolved by this firmware ⑤
- The planning status of a corresponding firmware update task can be:
- Not yet planned ③; clicking the link adds the firmware update task to the Task list
- Planned ④; the corresponding task is listed at the top of the Task list
If no update recommendation is available ⑥, a firmware update task can still be created – for example, for a new firmware version that does not address vulnerabilities.
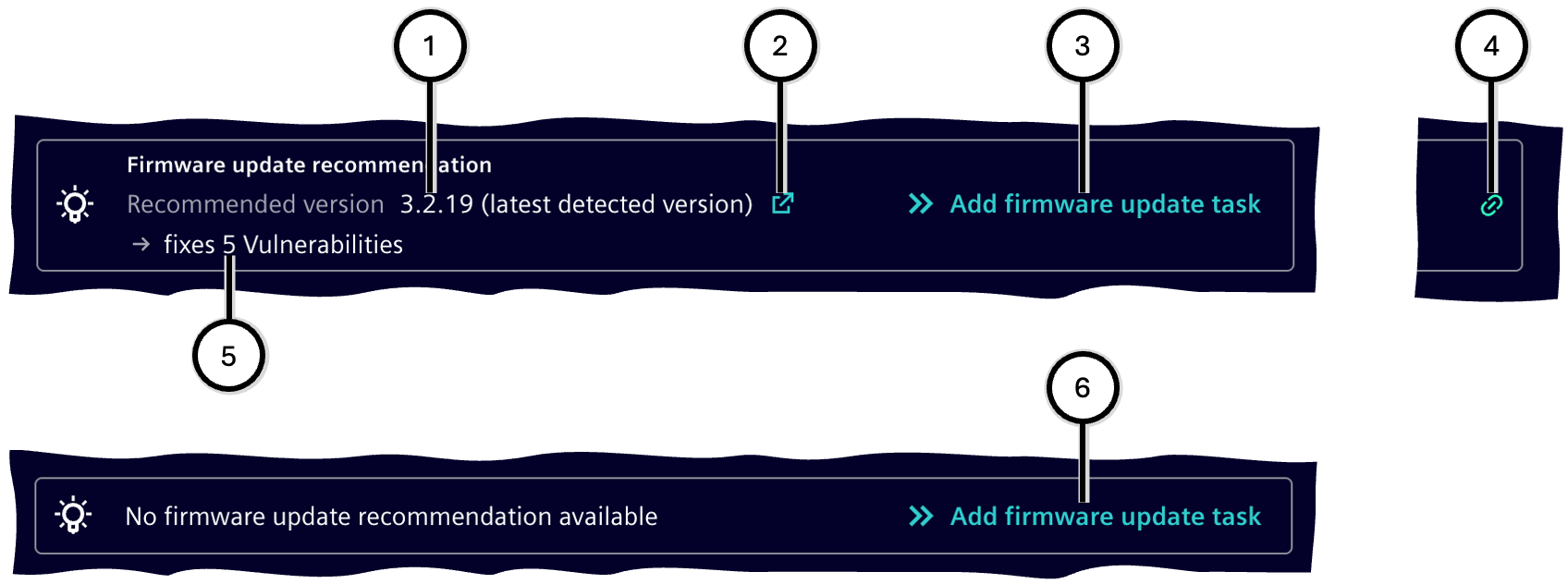
| Number | Description |
|---|---|
| ① | Version of the latest firmware |
| ② | Firmware update task is not yet planned |
| ③ | Optional: Link to the firmware download page |
| ④ | Firmware update task is planned |
| ⑤ | Number of vulnerabilities that can be resolved with this version |
| ⑥ | Representation in case no update recommendation is available |
Vulnerability list
A vulnerability can have one of the following statuses:
| Vulnerability Status | Description | Linked to Tasks | Automatic Resubmission | Status Group |
|---|---|---|---|---|
| Open | No decision has been made regarding this vulnerability yet | No | No | Active |
| Planned | At least one task is linked to this vulnerability | Yes | No | Active |
| Risk accepted till | The impact of this vulnerability is known and accepted | No | Yes | On hold |
| Remediation blocked | The vulnerability cannot be resolved due to current circumstances | No | Yes | On hold |
| Asset removal planned | The device is planned to be removed from the facility | No | No | On hold |
| Not relevant | This vulnerability cannot affect operations | No | Yes | Treated |
| Obsolete by implementation | This vulnerability is resolved through other planned tasks | No | No | Treated |
| Mitigated | This vulnerability has been mitigated through countermeasures | Yes | No | Treated |
| Fixed | This vulnerability has been resolved according to the manufacturer's recommendation | Yes | No | Fixed |
Each vulnerability can be expanded or collapsed.
When collapsed, it displays the following information:
- Button to expand ①
- Risk level of the vulnerability ② for the selected device – see Risk Level
- If the vulnerability is newly added since the last task publication ('New' ③) or if the publisher has updated the vulnerability description ('Updated' – e.g., from CVE version 1.2 to 1.3), this is indicated.
- Title of the vulnerability ④
- Current processing status of the vulnerability ⑤
When expanded, it displays the following information:
- All information from the collapsed view (the previous expand button is replaced by the collapse button ⑨)
- Publisher of the security advisory ⑥, vulnerability identifier ⑦ (clicking opens the vulnerability description in a sidebar), and the identifier of the security advisory ⑧ (clicking opens the advisory in a separate browser window).
- Description of the vulnerability ⑩
- Detection date on the device ⑬ and last update of the vulnerability ⑭
- Recommendations according to the vulnerability description, which may include 'Manufacturer's update recommendation' ⑪ (optionally with a link to the resource) and 'Workarounds and countermeasures' ⑫. Using button ⑯, a specific task can be created from a recommendation in the Task List< section and linked to this vulnerability; in this case, the button is replaced by a link symbol ⑮. If identical recommendations appear in other vulnerabilities of this device, they are automatically linked to the task as well, and the vulnerability status is set to "Planned."
For recently published vulnerabilities, it may happen that no recommendations are available – this is indicated accordingly ⑰ ⑱. Manufacturers often provide these later. For very outdated devices, it must be expected that they are no longer supported by the manufacturer.
The risk originating from a vulnerability can be accepted in order to temporarily remove it from vulnerability views and main statistics. An accepted risk is not remedied by that and may lead to exploiting the vulnerability or otherwise causing negative effects on the system. It's recommended to fix vulnerabilities and not accepting risks. After using the button to accept a risk ⑳, a justification for that ㉑ needs to be entered. Then the related vulnerability becomes moved into the status group 'On hold' ㉔. A vulnerability listed there shows the justification entered ㉕. The vulnerability can become reactivated ㉖, which moves it into the status group 'Active' ⑲ again.
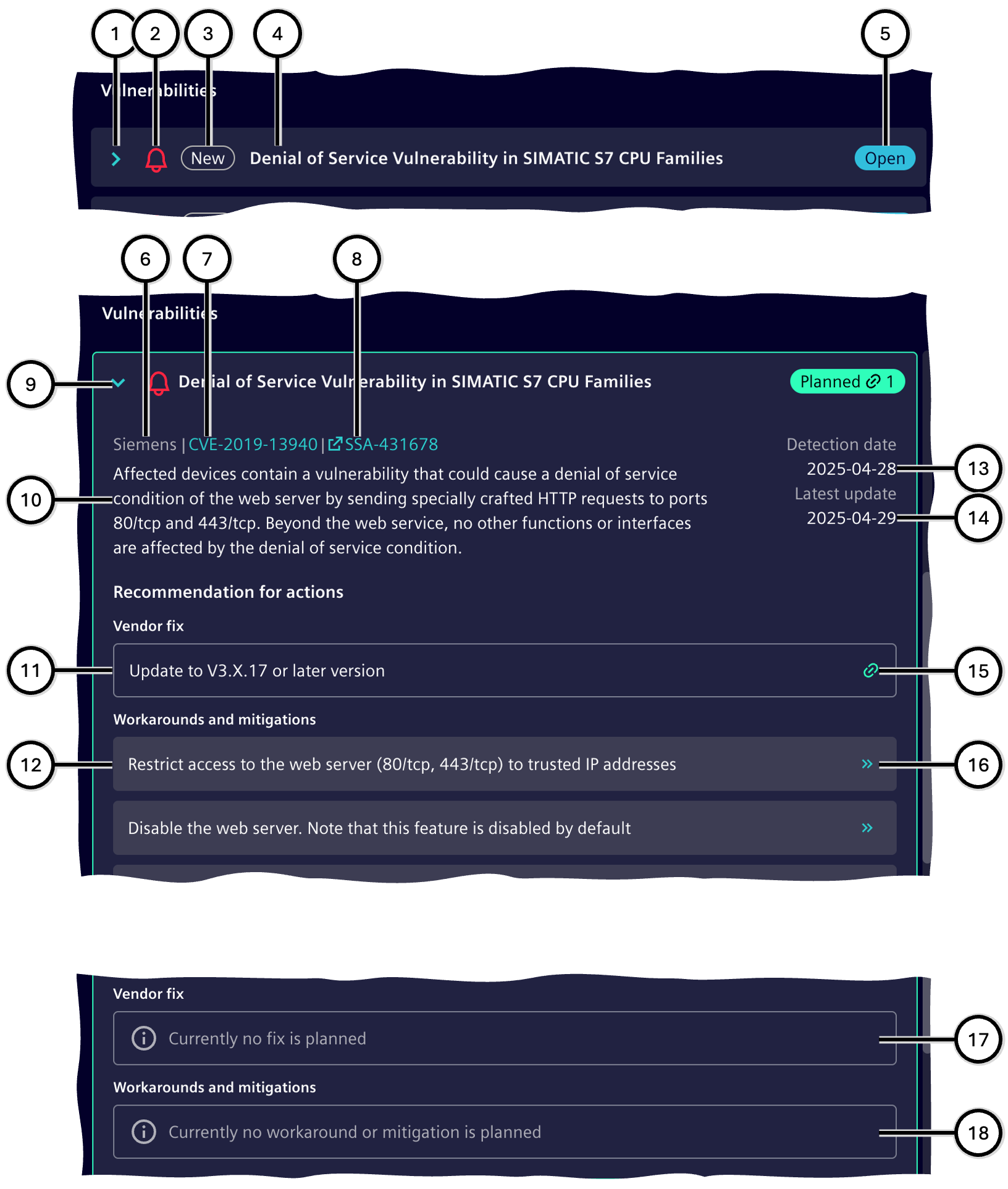
| Number | Description |
|---|---|
| ① | Button to expand the vulnerability information |
| ② | Risk level of the vulnerability for this device |
| ③ | Optional: Indication of changes since the last task publication |
| ④ | Title of the vulnerability |
| ⑤ | Processing status of the vulnerability |
| ⑥ | Publisher of the security advisory |
| ⑦ | Description of the vulnerability |
| ⑧ | Manufacturer's update recommendation |
| ⑨ | Button to collapse the vulnerability information |
| ⑩ | Description of the vulnerability |
| ⑪ | Manufacturer's update recommendation |
| ⑫ | Workarounds and countermeasures |
| ⑬ | Detection date on the device |
| ⑭ | Last update of the vulnerability |
| ⑮ | Indication that a corresponding task for this measure has already been created in the task area |
| ⑯ | Button to create a corresponding task in the task area |
| ⑰ | Representation in case no manufacturer's update recommendation is available |
| ⑱ | Representation in case no workarounds or countermeasures are available |
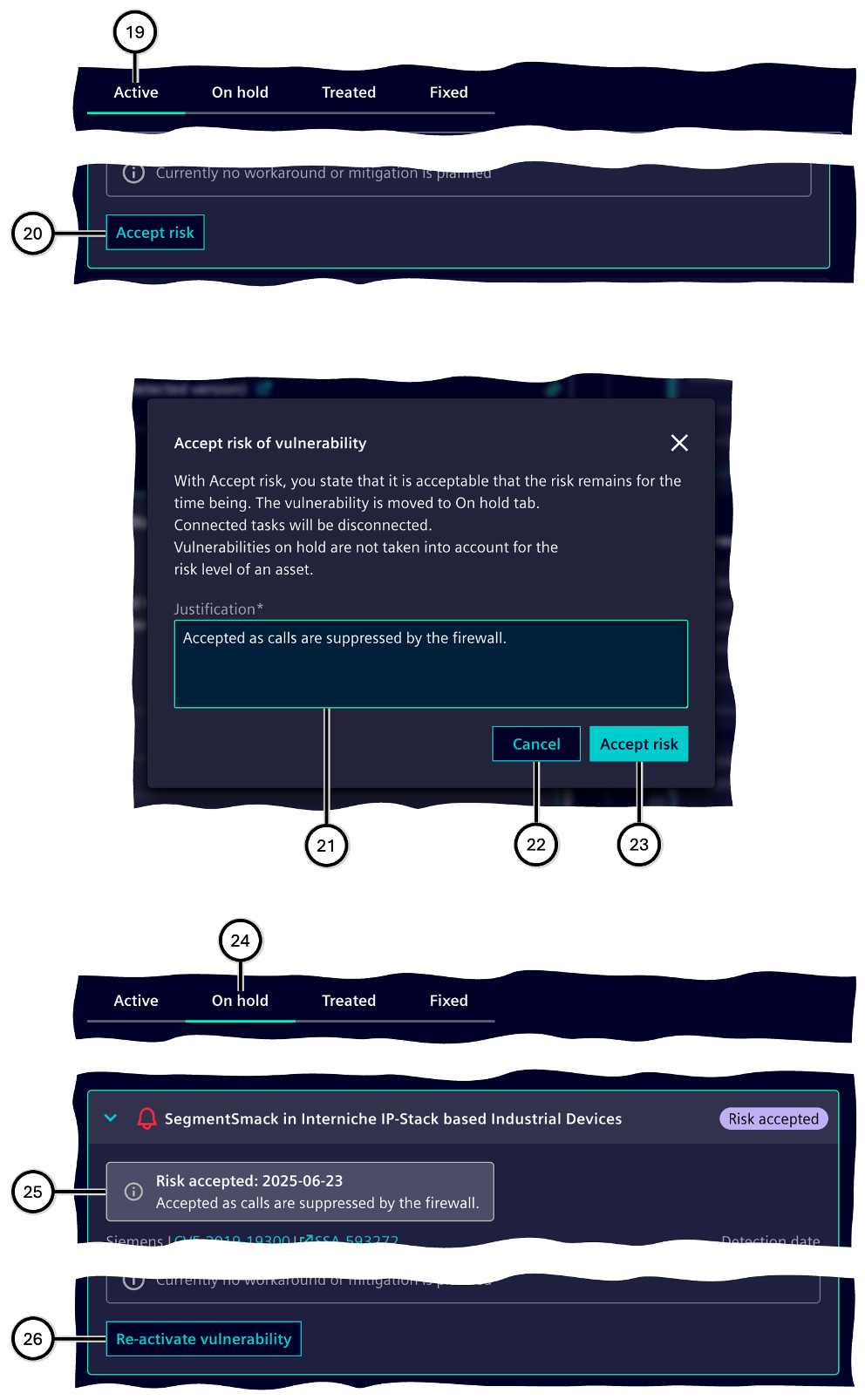
| Number | Description |
|---|---|
| ⑲ | Status group 'Active' chosen |
| ⑳ | Button 'Risk accepted' |
| ㉑ | Input field vor justification |
| ㉒ | Button to cancel |
| ㉓ | Button to accept the risk |
| ㉔ | Status group 'On hold' chosen |
| ㉕ | Hint on status change and reasoning |
| ㉖ | Button to reactivate the vulnerability |
Vulnerability can be marked as "Not relevant" if it is not applicable to the device, for example, because the device does not support the affected protocol or service. In this case, the vulnerability is moved to the status group 'Treated' and will no longer be displayed in the 'Active' status group.
Vulnerability can be marked as "Obsolete by implementation" if it is resolved by other tasks that have already been implemented. In this case, the vulnerability is moved to the status group 'Treated' and will no longer be displayed in the 'Active' status group.
Status group 'On hold'
This status group displays vulnerabilities for which just temporary decisions had been taken.
The functionality and operation largely follow the description of the 'Active' status group, with the following differences:
- The 'Firmware Update' object is not displayed.
- Tasks cannot be created.
- A vulnerability can be reactivated.
Status group 'Treated'
This status group displays vulnerabilities for which all associated 'Workarounds and Countermeasures' tasks have been implemented.
The functionality and operation largely follow the description of the 'Active' status group, with the following differences:
- The 'Firmware Update' object is not displayed.
- Tasks cannot be created.
- A vulnerability can be reactivated.
Status group 'Fixed'
This status group displays vulnerabilities for which the manufacturer's update recommendation has been implemented.
The functionality and operation largely follow the description of the 'Active' status group, with the following differences:
- The 'Firmware Update' object is not displayed.
- Tasks cannot be created.
- A vulnerability can no longer be reactivated.
Task list
This section displays all tasks defined for the affected device (see Asset information<). For each task, the vulnerabilities it is linked to are shown. Additionally, custom tasks ④ can be created here. Messages ⑤ inform about important information, and can be closed ⑥.
Four different types of tasks are possible:
| Number | Task Type | Content | Options |
|---|---|---|---|
| 1 | Firmware Update ① | Version of the firmware to be installed; the latest security-relevant version is preselected | Selection of the firmware version to be installed |
| 2 | Manufacturer's Update Recommendation ② | Corresponding text according to the vulnerability description | - |
| 3 | Workarounds and Countermeasures ③ | Corresponding text according to the vulnerability description | - |
| 4 | Custom Task ④ | Description of the custom task | Text input; the task cannot be added without text |
There can only be none or one task of task type 1 in the Task list; tasks of types 2, 3, and 4 can be included in any number.
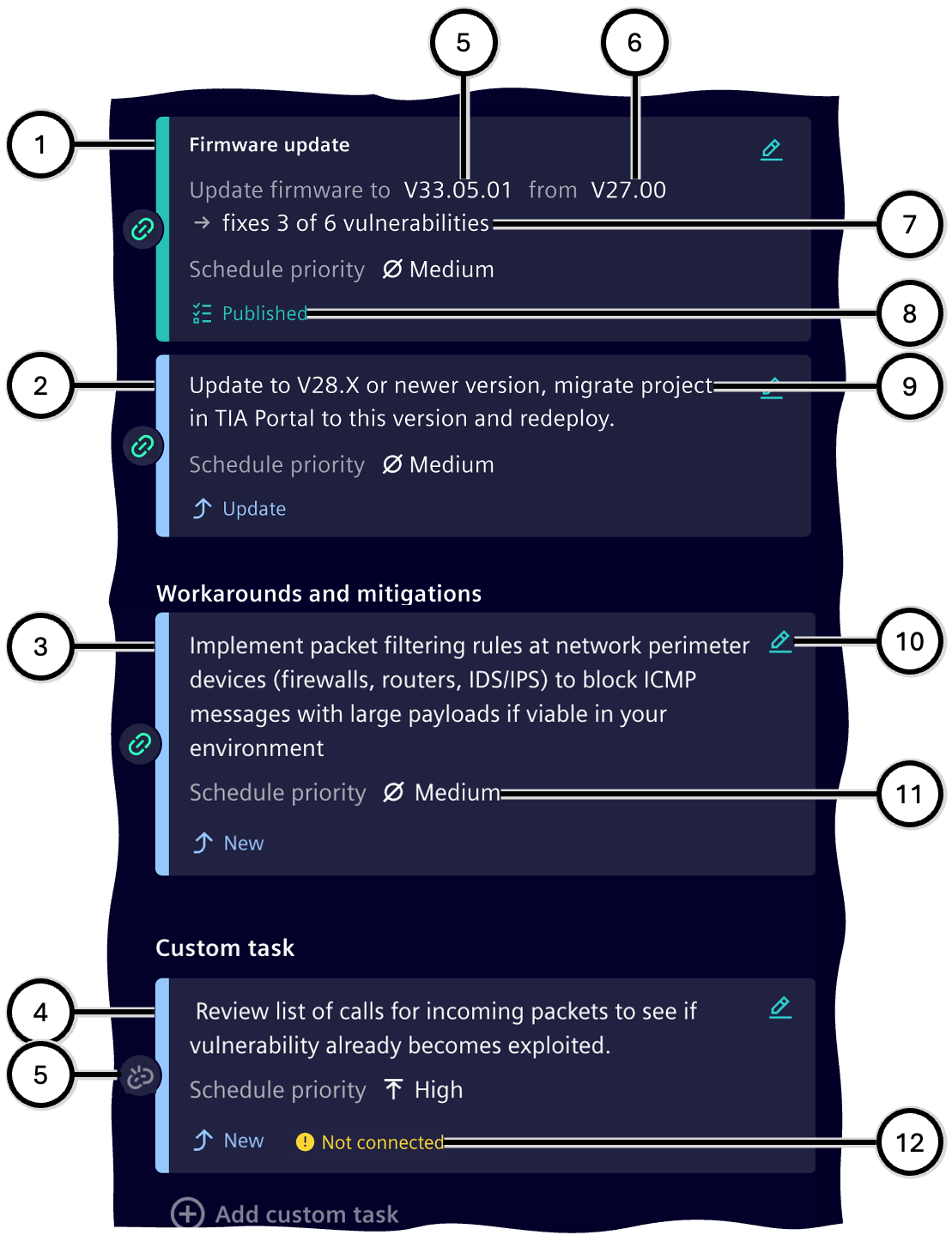
| Number | Description |
|---|---|
| ① | Task of type 'Firmware update' |
| ② | Task of type 'Manufacturer's update recommendation' |
| ③ | Task of type 'Workarounds and mitigations' |
| ④ | Task of type 'Custom task' |
| ⑤ | Optional: Notice about the blocking of tasks for this device in Task management |
| ⑥ | Optional: Button to remove the notice |
| ⑦ | Button to edit the task |
| ⑧ | Optional: Labels for the firmware version to be installed and the previous version |
| ⑨ | Publication status of the task |
| ⑩ | Description of the task |
| ⑪ | Selected scheduling priority |
| ⑫ | Connection status of the task with the selected vulnerability |
| ⑬ | Optional: Notice that the task is not connected to any vulnerability |
Editing tasks
A newly created task is in edit mode. Here, the priority ⑫ can be set, or the task can be removed ⑬. Depending on the task type, data from a predefined list can be selected, or free text can be entered or modified.
Once the task's contents are set as desired ①/⑥, clicking outside the task exits the edit mode and saves the changes ②/⑦.
By using button ⑭, the edit mode can be reopened.
Tasks with the status "New" are only visible in the Task list, but not in the Task Management. Tasks in status "Update" still - in the Task Management - contain the last published data. To transfer the now modified data to the Task Management, it has to become published again. As long as data becomes edited in the Task list and has not yet been published to the Task Management, tasks of this asset cannot be shown in Task Management; a message in both Task list ⑨ and Task Management points that out. This message can temporarily become removed ⑩.
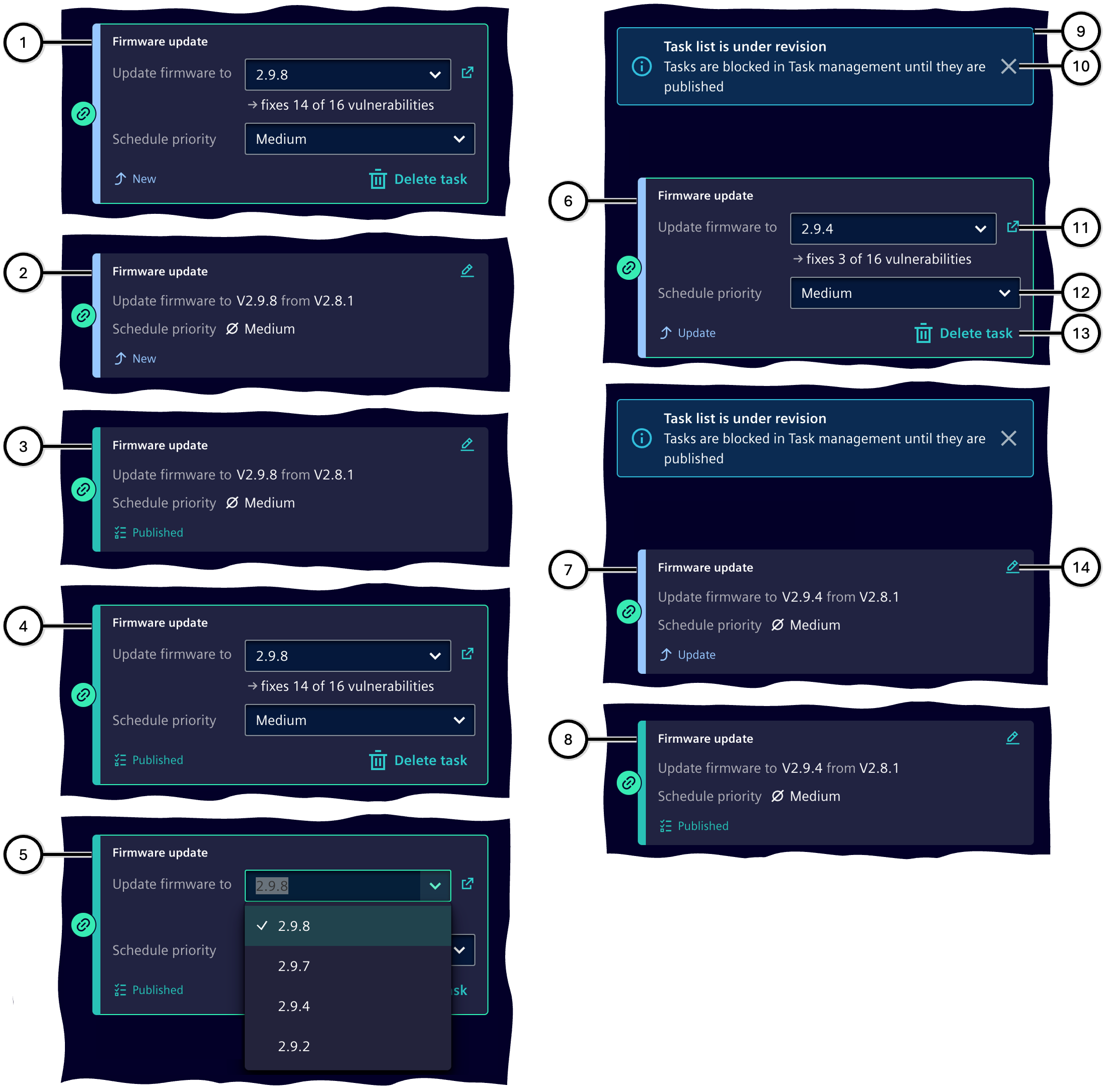
| Number | Description | Status in Task list | Task data in Task list | Task data in Task Management |
|---|---|---|---|---|
| ① | New task in edit mode | New | As shown | (Not available) |
| ② | Created task | New | Like ① | (Not available) |
| ③ | Published task | Published | Like ① | Like in Task list ① |
| ④ | Previously created task, reopened in edit mode | Published | Like ① | Like in Task list ① |
| ⑤ | Previously created task, reopened in edit mode; e.g., selection options | Published | Like ① | Like in Task list ① |
| ⑥ | Previously created task, reopened in edit mode – unpublished changes | Update | As shown | Like in Task list ① |
| ⑦ | Edited task – unpublished changes | Update | Like ⑥ | Like in Task list ① |
| ⑧ | Published task | Published | Like ⑥ | Like in Task list ⑥ |
| ⑨ | Optional: Notice about task blocking for this device in Task Management | - | - | - |
| ⑩ | Optional: Button to remove the notice | - | - | - |
| ⑪ | Optional: Button to display additional information | - | - | - |
| ⑫ | Selection field for task priority | - | - | - |
| ⑬ | Button to delete the task | - | - | - |
| ⑭ | Button to edit the task |
Selecting priority
The priority of a task is important for further processing and planning in Task Management. Every newly created task is automatically assigned a medium priority, which can then be adjusted as needed. To select the priority of a task, switch to the task's edit mode, open the priority menu, and choose the desired priority.
Removing a task
A task that is no longer needed can be removed from the Task list. It will no longer contribute to the processing of vulnerabilities, which may affect the status of vulnerabilities and the Managing status. To remove a task, switch to the task's edit mode and select the button to delete it.
Connecting vulnerabilities and tasks
Connecting vulnerabilities and tasks ensures that the implementation of a task can be checked to determine whether the vulnerability has been resolved. A vulnerability is considered...
- treated, when all 'Workarounds and mitigations' tasks linked to the vulnerability have been implemented.
- fixed, when the manufacturer's update recommendation has been implemented.
Connecting is managed as follows:
- A vulnerability must always be selected to create a task.
- When adding a 'Manufacturer's Update Recommendation' or a 'Workaround and mitigations' from a vulnerability description (see Vulnerability List<), the connection between the vulnerability and the task is automatically established.
- Manually creating a task is only possible if a vulnerability is selected; the manually created task is then automatically connected to this vulnerability.
- Clicking the connection indicator ①/②/③/④ toggles between the connection states 'connected' ①/② and 'not connected' ③/④; any connections to other vulnerabilities remain unaffected.
Note
The connection status can be changed without entering edit mode.
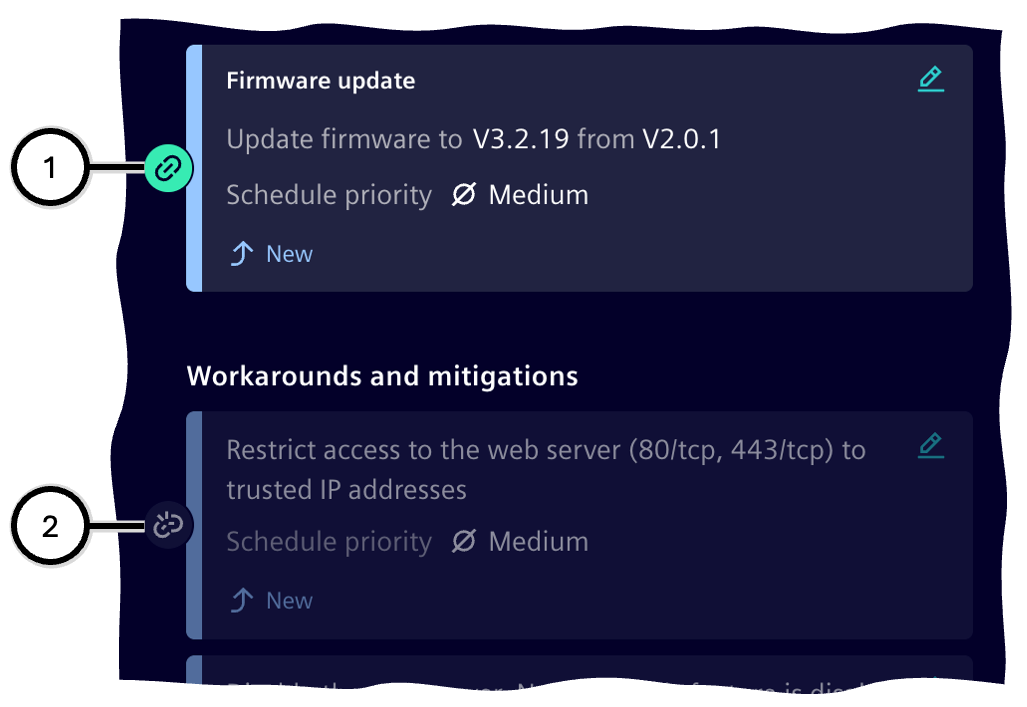
| Number | Connection Status | Description |
|---|---|---|
| ① | Connected | Task is connected to the currently selected vulnerability |
| ② | Connected | No vulnerability is currently selected; the task is connected to at least one vulnerability |
| ③ | Not connected | Task is not connected to to the currently selected vulnerability, but to another vulnerability |
| ④ | Not connected | Task is not connected to any vulnerability |
Task publication status and overview
Tasks can have one of these statuses:
| Task Publication Status | Representation | Meaning | Task Editable | Task Visible in Task Management |
|---|---|---|---|---|
| New | Task has been defined but not yet published | Yes | No | |
| Published | Task has been published and is now visible in Task Management | Yes | Yes | |
| Updated | Already published task has been modified; the change must be published to be visible in Task Management | Yes | No | |
| Implemented | Already published task has been executed | No | No | |
| Not connected | Task is not connected to a vulnerability | Yes | No |
In the 'Active' status group, a summary aggregates tasks by status: the number of new or updated tasks ③, which only take effect after publication, and the number of already published tasks ④.
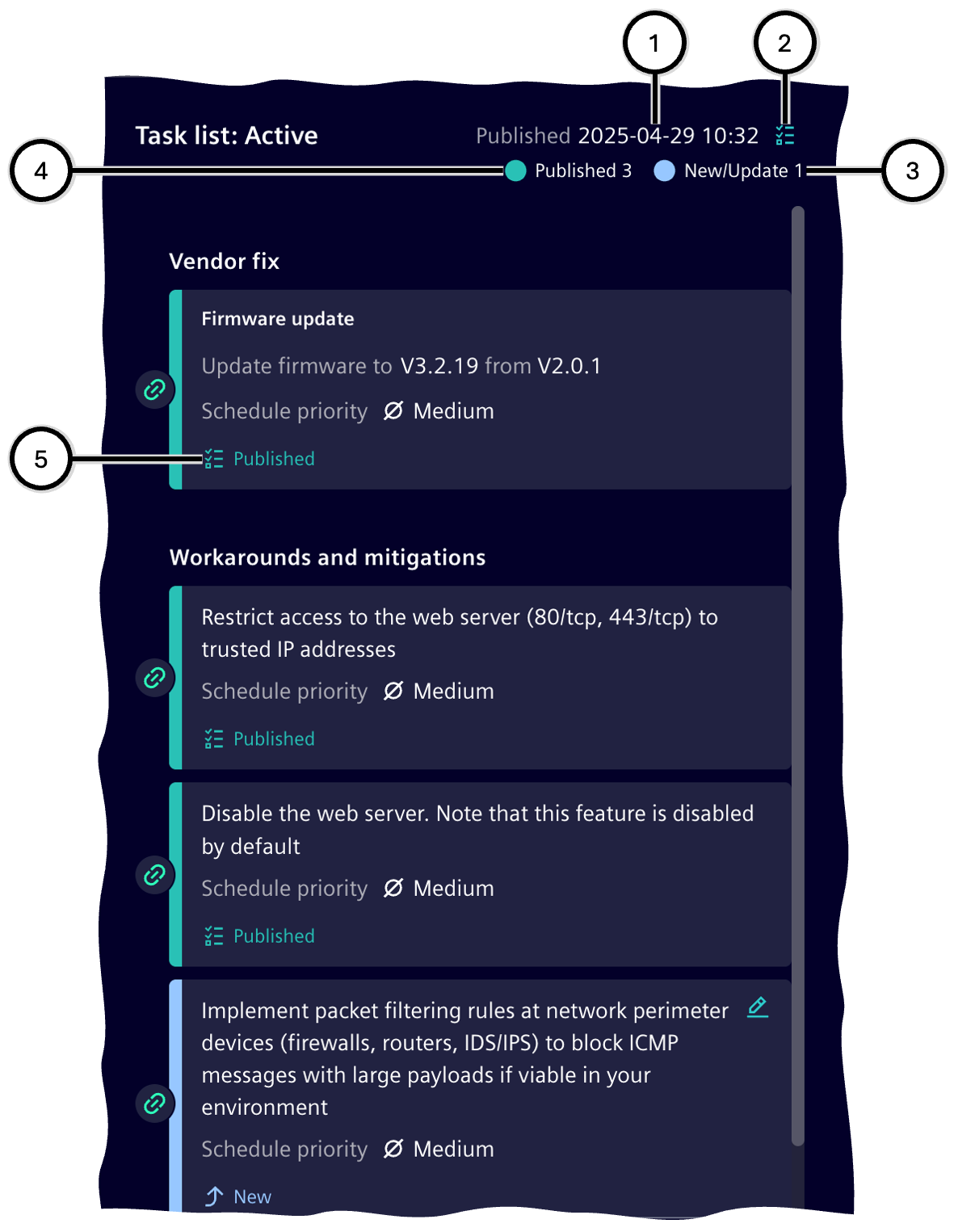
| Number | Description |
|---|---|
| ① | Date of the most recent publication of tasks in this Task list |
| ② | Button to switch to Task Management |
| ③ | Number of tasks not yet published |
| ④ | Number of published tasks |
| ⑤ | Publication status of the task |
Managing progress and additional functions
The Managing progress ① shows the ratio between vulnerabilities in the 'Planned' state and those in the 'Open' state. All other vulnerabilities are no longer considered here, as they have already been resolved or addressed by other solutions.
The button ② is used to publish all tasks and, if applicable, creation, update, and deletion requests for tasks in Task management. At this point, all necessary tasks for this device are considered defined and can no longer be changed. The further procedure with these tasks is described in the chapter Task Management. Unpublished tasks are not found in Task management and therefore cannot be completed.
Note If the device for which tasks are being processed in the Device focus is simultaneously viewed in Task management – for example, by other users – the task area in Task management will be locked. Only when task processing in the device focus is completed will the tasks in Task management be released for use again.

| Number | Description |
|---|---|
| ① | Managing progress of all vulnerabilities for this device |
| ② | Button to publish all tasks in the Task list |